Connect to Mikrotik via SSH and start writing text below
Set global VARs
:global COMMONNAME "openVPN"
:global COUNTRY "UA"
:global STATE "KV"
:global LOCALITY "Kyiv"
:global ORG "My org"
:global UNIT ""
:global KEYSIZE "1024"
:global USERNAME "admins"
:global PASSWORD "8charsPassword"
:global NET "77"
:global PORT "7777"Make server and client CRT
/certificate add name=ca-template country="$COUNTRY" state="$STATE" locality="$LOCALITY" organization="$ORGANIZATION" unit="$UNIT" common-name="$COMMONNAME" key-size="$KEYSIZE" days-valid=3650 key-usage=crl-sign,key-cert-sign sign ca-template ca-crl-host=127.0.0.1 name="$COMMONNAME" :delay [6] add name=server-template country="$COUNTRY" state="$STATE" locality="$LOCALITY" organization="$ORGANIZATION" unit="$UNIT" common-name="server@$COMMONNAME" key-size="$KEYSIZE" days-valid=3650 key-usage=digital-signature,key-encipherment,tls-server sign server-template ca="$COMMONNAME" name="server@$COMMONNAME" :delay [6] add name=$USERNAME country="$COUNTRY" state="$STATE" locality="$LOCALITY" organization="$ORGANIZATION" unit="$UNIT" common-name="$USERNAME" key-size="$KEYSIZE" days-valid=3650 key-usage=tls-client sign $USERNAME ca="$COMMONNAME" name="$USERNAME"
Create pool, profile, interface, firewall
/ip pool add name=VPN-POOL-devops ranges="10.$NET.1.2-10.$NET.1.254" /ppp profile add dns-server="10.$NET.1.1" local-address="10.$NET.1.1" name=VPN-PROFILE remote-address=VPN-POOL use-encryption=yes /interface ovpn-server server set auth=sha1 certificate="server@$COMMONNAME" cipher=aes128,aes192,aes256 default-profile=VPN-PROFILE enabled=yes require-client-certificate=yes port="$PORT" max-mtu=1460 /ip firewall filter add chain=input dst-port=$PORT protocol=tcp comment="Allow OpenVPN" action=accept place-before=0 add chain=input action=accept protocol=tcp src-address=10.$NET.1.0/24 in-interface-list=dynamic log=no log-prefix="" place-before=2 /ppp secret add name=$USERNAME password=$PASSWORD profile=VPN-PROFILE service=ovpn /certificate add name="$USERNAME-to-issue" copy-from="$USERNAME" common-name="$USERNAME@$COMMONNAME" sign "$USERNAME-to-issue" ca="$COMMONNAME" name="$USERNAME@$COMMONNAME" /certificate export-certificate "$COMMONNAME" export-passphrase="" export-certificate "$USERNAME@$COMMONNAME" export-passphrase="$PASSWORD"
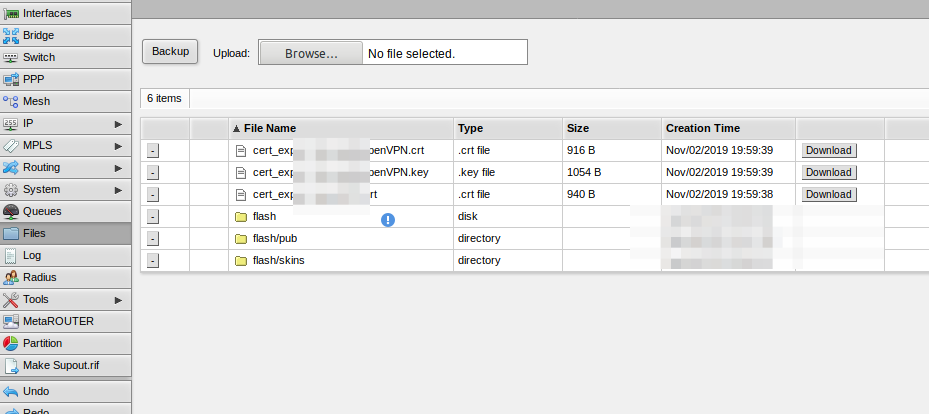
Goto menu Files in Mikrotik admin panel and download ca.crt + client.crt + client.key
Then make file SomeName.ovpn with content:
client # в этой строчке мы указываем адрес в интернете нашего микротика remote <your.server.IP> <Port> dev tun proto tcp tun-mtu 1460 nobind persist-key persist-tun keepalive 10 120 verb 3 cipher AES-256-CBC auth SHA1 remote-cert-tls server # эта строка задаёт файл с логином-паролем которые мы прописывали в PPP-Secrets на микротике auth-user-pass auth.cfg # в этой части мы задаём настройки сетей которые находятся за микротиком, # а 172.21.108.1 это адрес микротика который мы указывали в PPP профиле #route-method exe #route-delay 2 #route 192.168.1.0 255.255.255.0 172.21.108.1 #for internet access redirect-gateway autolocal <ca> -----BEGIN CERTIFICATE----- .....Put your ca crt from downloaded files..... -----END CERTIFICATE----- </ca> <cert> -----BEGIN CERTIFICATE----- .....Put your client crt from downloaded files..... -----END CERTIFICATE----- </cert> <key> -----BEGIN RSA PRIVATE KEY----- .....Put your client key from downloaded files..... -----END RSA PRIVATE KEY----- </key>
Put your key and crt and change host:port vars
and file auth.cfg
user pasword
with this two files you can start client